Today I planned another IFR flight from EHLE to EHRD and back. This time my wife is also with me. I got the PPR for the IFR departure and arrival for EHLE. I am going again with the PHWOH:

There was a helicopter also doing some flying at the airport:

I filled a FL060 INKET departure but the freezing level was too low for that so I said that I have a change in flightplan at startup requesting 3000ft instead. This was not a problem. After I got my startup I checked the autopilot. That did not want to engage. Not sure why said something about a data path or something. Anyway, I decided I would continue with the flight anyway, as this is not a no-go item (for a longer flight I likely would have cancelled).
After take off and climbing to 3000ft you can see here that we are more or less at the cloud base.

After passing ASBES I got a “direct PELUB”. While heading south we did end up in the clouds momentarily (for maybe a minute or so).
When approaching PELUB I got offered a “direct REWIK”, which I accepted (as it is shorter). Then I was told the ILS was out for runway 24, and got offered a choice of approaches. I took the RNP24. It did not matter much actually as I was in VMC at that point. Once on the ground I exited via V3 (I did not want to break too hard to make V4, and I also did not hear that anybody was behind me on an approach). While exiting we could see the commercial aircraft parked on the apron:

We had to continue taxi on V to L where the aeroclub is situated (I arranged that I could get handling from them).
When approaching the end of L we saw the follow me car, then somebody got out and guided us to the parking spot. After getting out paying the landing fee, having a cup of coffee it was time to get back in the aircraft. When asking for a startup I immediately got my IFR clearance (an INKET departure). Before take-off I got offered a right turn direct to INKET instead, which I accepted. Gives us a nice view of the city of Rotterdam:

However, this later gave me a bit of an issue in the sense that I was too early for my landing slot at EHLE. I pretty much had no choice other then to do a VFR approach. So I cancelled my IFR when getting close to the EHLE CTR. I still had to fly around the CTR and below the TMA to get to the VFR arrival route Mike. When approaching Mike I saw other aircraft converging on Mike. So I called EHLE tower a bit early, just such that I could hear the other aircraft and they could hear me. Shortly after I contacted tower, I could hear another aircraft contact tower as well. They were warned of us. I reported Mike then few mins later I got offered a direct base to runway 23, which I accepted.
Here is the track to EHRD:
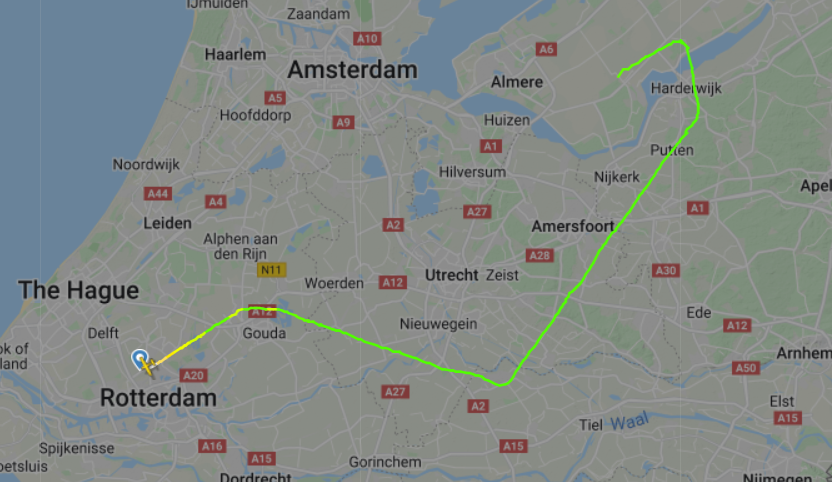
The 1st part of the flight is not shown (too low)
Track back to EHLE:
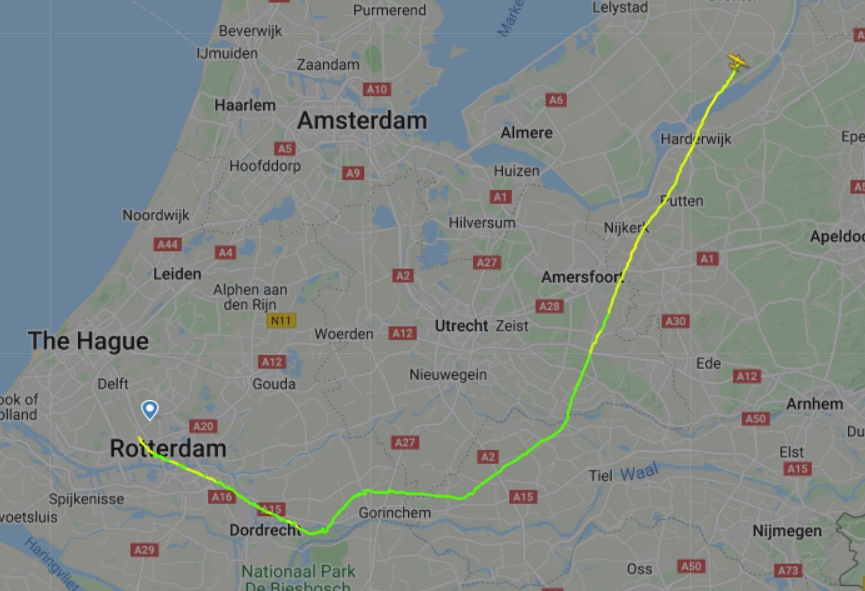
The last part is not shown because I was descending to get below the TMA.
My next flight is going to be my prof check for my instrument rating.